March 2021

Product Spotlight
On Privacy Protection Solutions
By Maria Henriquez, Associate Editor
Digital Shadows
Helps Reduce Digital Risk
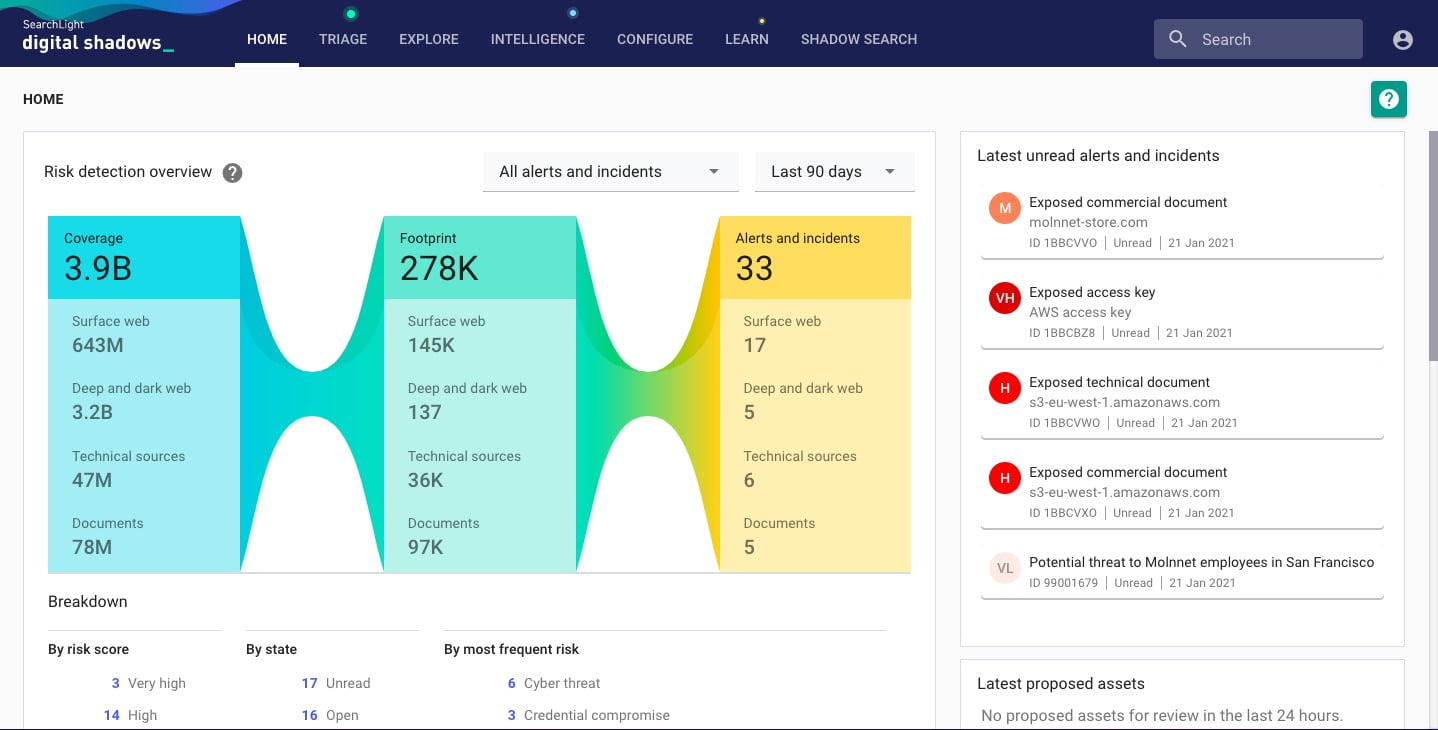
Digital Shadows’ SearchLight continuously identifies where digital assets (data, websites and social media accounts) are exposed, providing sufficient context to understand the risk, and options for remediation. Organizations use SearchLight to help reduce digital risk and enable the organization to take control of its digital footprint and limit the opportunities of adversaries. SearchLight has four main stages. At each of these stages, SearchLight acts as an extension of the security team to help configure key assets, collect from hard-to-reach sources, analyze and identify risks, and mitigate the impact. Image courtesy of Digital Shadows
Find out more at www.digitalshadows.com
MediaPro
Ensures Security and Privacy Compliance
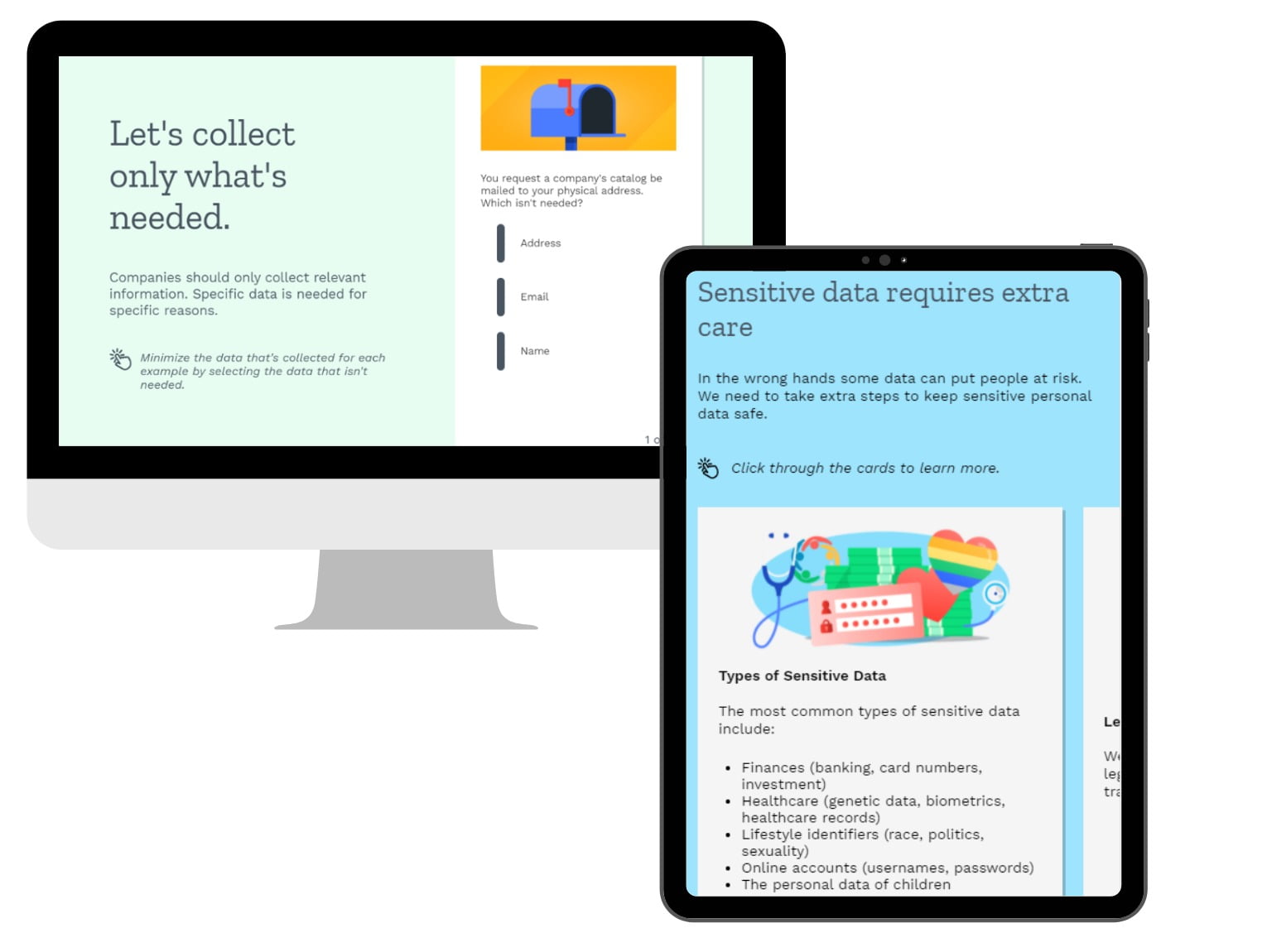
Paradigm by MediaPro is data privacy training that puts people first. The platform focuses on positive action and making an emotional connection with the learner. Paradigm is built to engage and inspire employees with modern and diverse imagery. Using language presented in layperson’s terms, Paradigm leaves out overly technical jargon to better connect with all employees. The solution covers the most important security and data privacy topics an organization needs to meet most security and compliance requirements. Image courtesy of MediaPro
Find out more at www.mediapro.com/paradigm
New Net Technologies
Spots Cyber Threats and Identifies Suspicious Activity
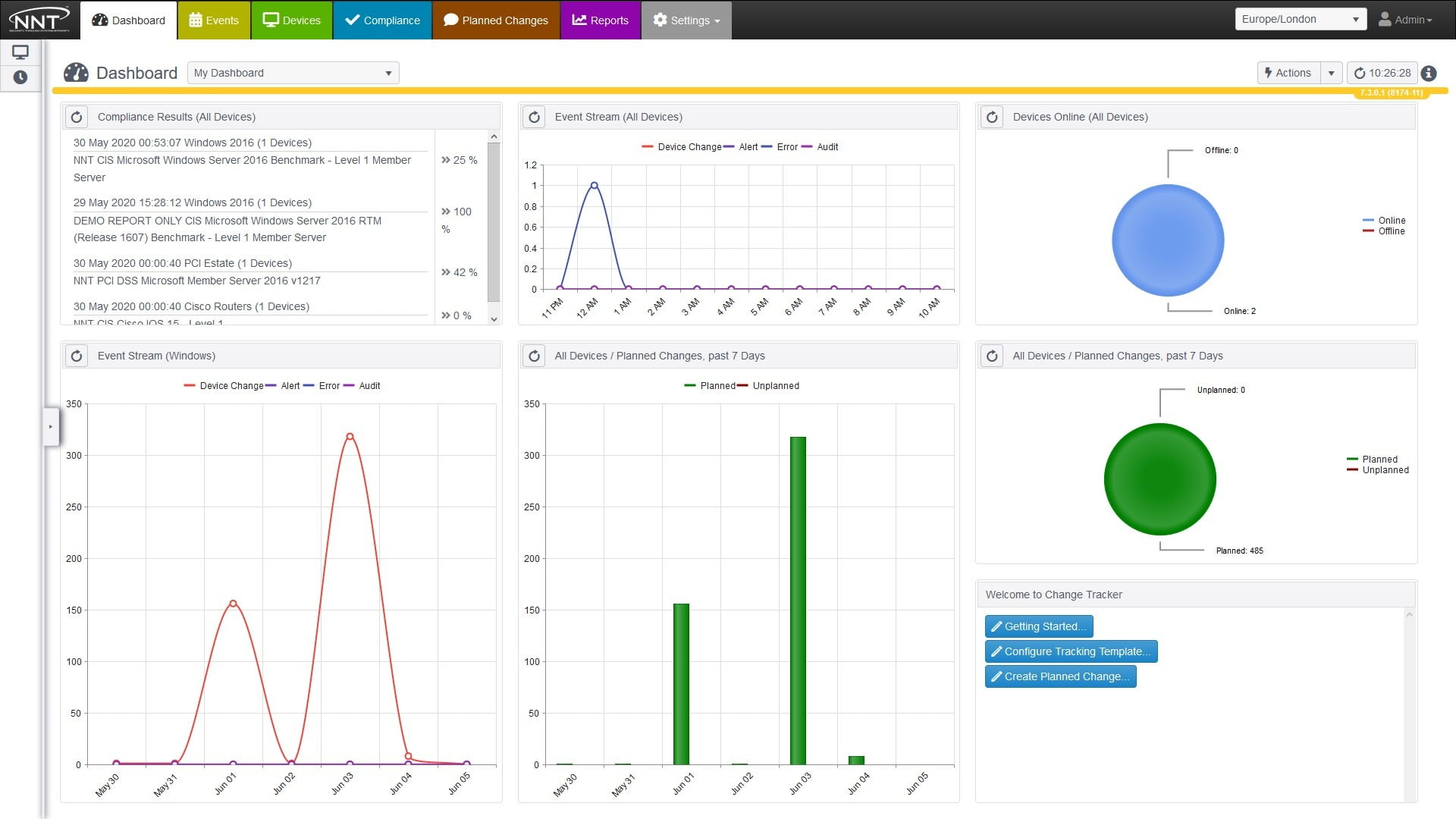
New Net Technologies Change Tracker Gen 7 R2 provides critical and fundamental cybersecurity prevention and detection. It does this by leveraging the required security best practice disciplines of system configuration and integrity assurance combined with the most comprehensive and intelligent change control solution available. Change Tracker from NNT will ensure that IT systems remain in a known, secure and compliant state at all times. NNT Change Tracker includes context-based File Integrity Monitoring and File Whitelisting to assure all change activity is automatically analyzed and validated. Complete and certified CIS and DISA STIG configuration hardening ensures all systems remain securely configured and, coupled with intelligent change control technology, provides noise reduction. Image courtesy of New Net Tech
Find out more at www.newnettechnologies.com
Thycotic
Protects Privileged Accounts
Thycotic Secret Server provides privileged access management (PAM) to organizations around the world and empowers them to securely monitor, manage and defend their most critical identity accounts and credentials. Built to support cloud deployment, Secret Server has been designed to integrate into organizations’ existing cybersecurity fabric. Secret Server Cloud enables organizations to discover, manage and delegate access to privileged accounts intelligently with role-based access controls, military-grade encryption, multi-factor authentication support, and centralized administration; meet cybersecurity PAM best practices and regulatory obligations with immutable auditing and reporting, and event-driven email alerts; and experience rapid time-to-value, with simple installation and an intuitive administration experience that empowers security professionals to configure and manage their PAM solution on their own terms. Image courtesy of Thycotic
Find out more at thycotic.com
SPHERE Technology Solutions
Safeguards Sensitive Data From Unauthorized Access
With an increased focus on protecting data from unauthorized access and all the data privacy regulations that are being enforced, organizations are now proactive in safeguarding their most sensitive data. SPHEREboard by SPHERE Technology Solutions helps organizations ensure only the appropriate personnel have access to only the data they need for their job functions. The solution provides visibility into all data access, highlighting violations, and automates the remediation of inappropriate entitlements. SPHEREboard utilizes an analytics-driven approach to finding owners of data, systems and assets; ensuring there is an authoritative source for governance processes, which is a vital requirement to implement a Least Privileged Access model and foundational for proper data privacy requirements, along with overall risk mitigation and breach prevention. Image courtesy of SPHERE Tech Solutions
Find out more at www.sphereco.com
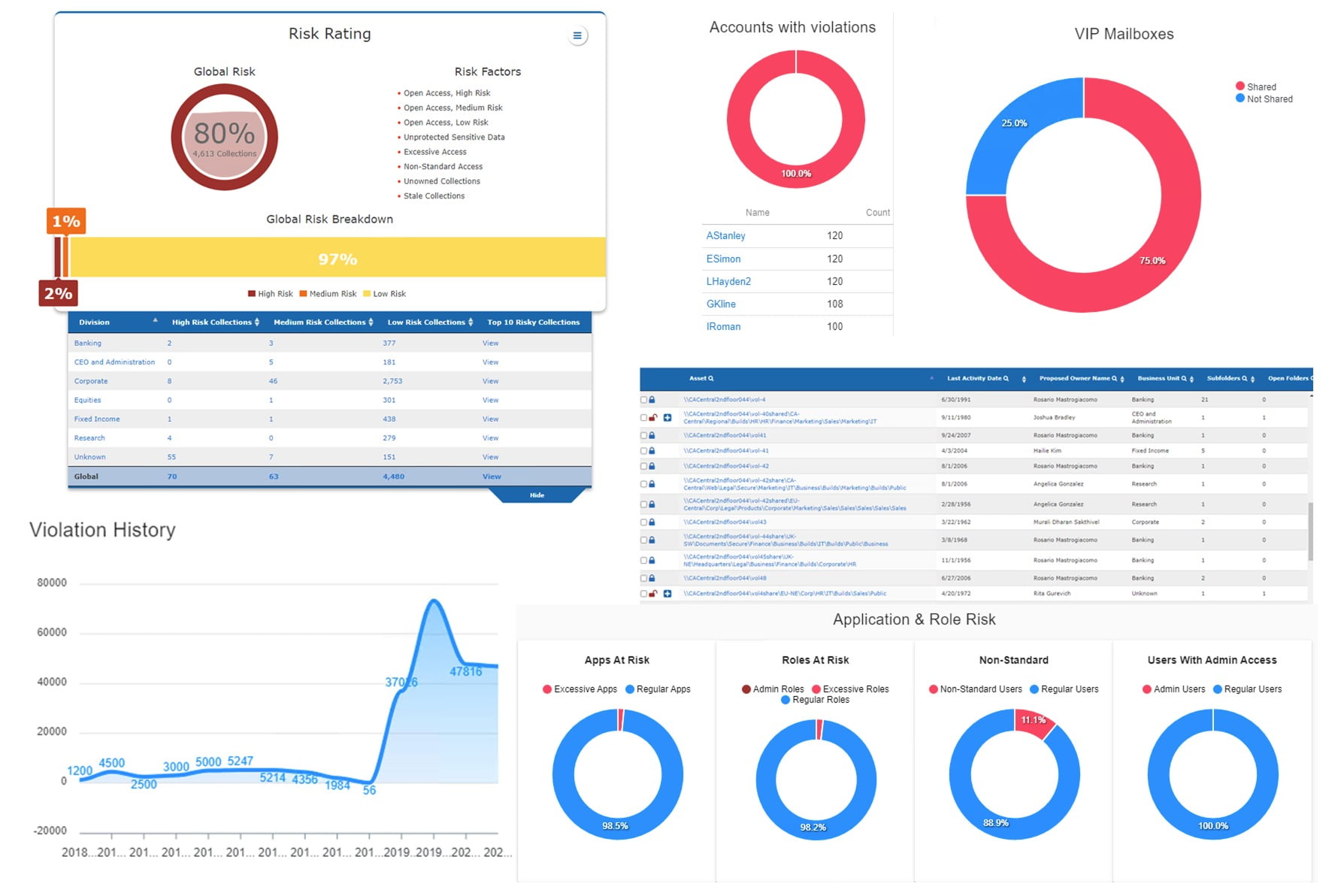
Concentric
Offers Data Protection Across Structured and Unstructured On-Premises
Concentric announced the latest advancements in its Semantic Intelligence data access governance solution for autonomous identification and risk assessment of inappropriate access, data sharing and user interactions – now with insights into user-related risks and support for both structured and unstructured data. The solution includes User360, a user-oriented lens into business-critical data. The User360 interface highlights risks associated with specific users to spot overly broad access privileges, inappropriate activity and wrong storage locations. The capability protects business-critical content – including PII/PCI, customer data, intellectual property and more – from compromised accounts, insider threats and careless employees. Image courtesy of Concentric
Find out more at www.concentric.ai
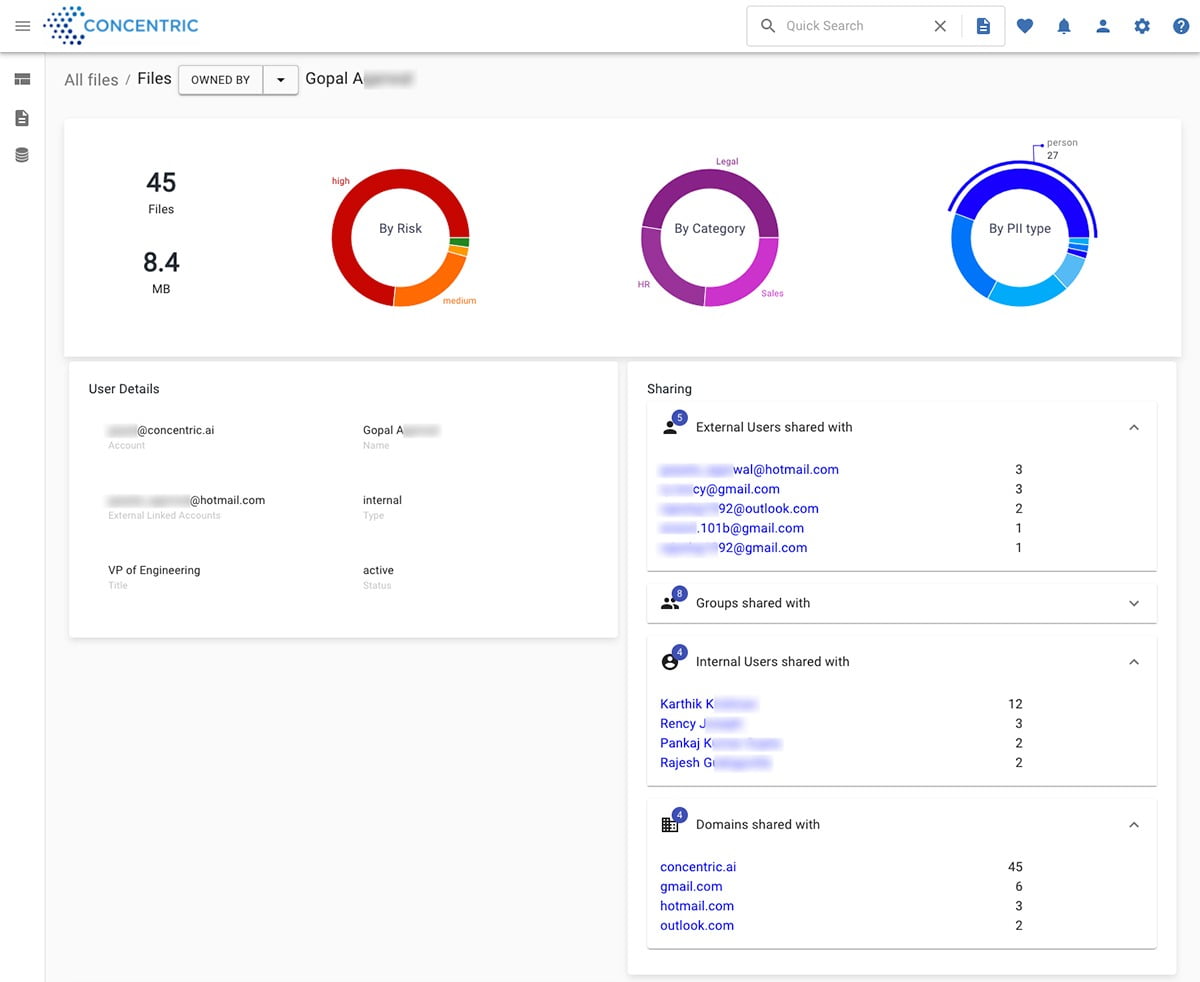
TetherView
Simplifies IT Infrastructure and Secures Data Sharing
TetherView’s Digital Bunker is a one-way-in and one-way-out private cloud solution targeted at businesses, governmental institutions and industries dealing with sensitive and private information. The Digital Bunker enables businesses to provide employees with a trusted, secure virtual environment, custom-tailored to their specific industry and compliance requirements. Through Digital Bunker, businesses can see, touch, audit, and prevent access to sensitive data, while providing employees with a scalable high-performance workspace. Pricing is a flat fee per user and is scalable based on performance requirements. Digital Bunker enables businesses to simplify IT infrastructure by integrating all of the IT services that businesses need within one platform, including security, compliance, disaster recovery, mobility and more. Image courtesy of TetherView
Find out more at tetherview.com
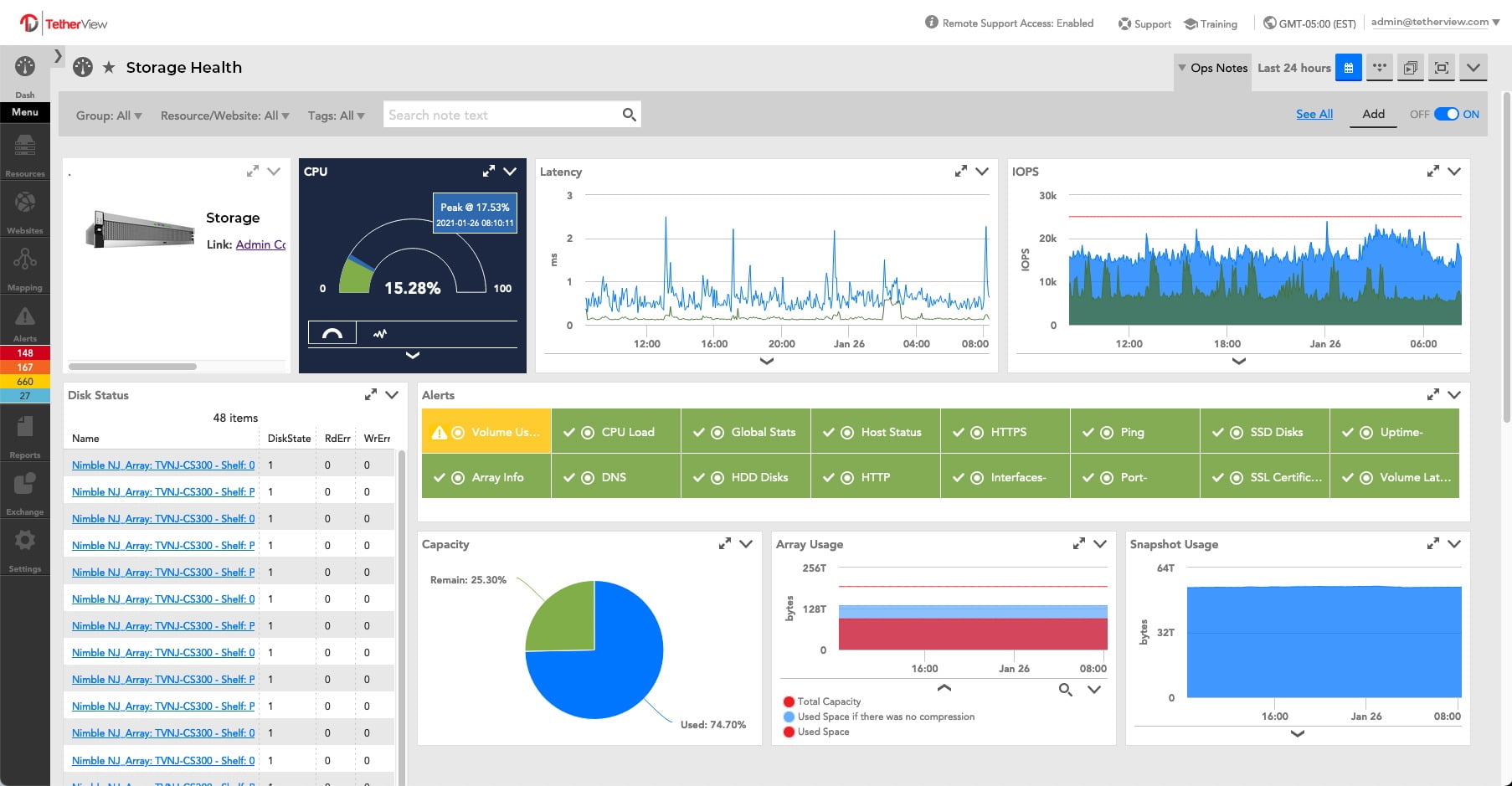
Lookout
Secures Digital Lives
At the highest level, the goal of a security team is to prevent data from being stolen. This is true of all data including intellectual property, personally identifiable data (PII), and product development and acquisition strategies. The Lookout security platform protects against attacks and enables the enterprise to detect and respond rapidly when there is a threat. The solution provides the right telemetry data to identify a cyberattack, know what the attacker is doing and proactively contain them. The security platform continually assesses the risk profile of devices to dynamically change Zero Trust access controls to protect data. Image courtesy of Lookout
Find out more at www.lookout.com/products/personal
march 2021 | securitymagazine.com


