july 2022


By Maria Henriquez, Associate Editor
Security operations are a critical priority for organizations and their executives. Yet, nearly one-third of executives treat security operations as either a low priority — important only during a crisis, or a medium priority — existing primarily to satisfy compliance and regulatory requirements, according to the Topo.ai 2022 Security Operations Benchmark Study, which surveyed security operations professionals, with 84% of the participants in an executive or leadership role.
Executive support and buy-in is an organizational attribute widely regarded as essential to success, the report found. A key question in the 2022 SecOps Benchmark Study examined how senior executives prioritize security operations. Seventy percent of those executives indicate their security operations (SecOps) are a critical or high priority for their organization’s executives. In contrast, 30% of participants indicated that SecOps is a low or medium priority for their senior executives.
Executives ranked the importance of their operational objectives, which are related to the tasks performed within the SecOps team and are primarily related to efficiency. Only the top three operational objectives (seen below) are ranked as critical by more than 50% of study participants.

Executive Support Highly Correlates With Security Operations Success
Yuri_Arcurs / E+ via Getty Images
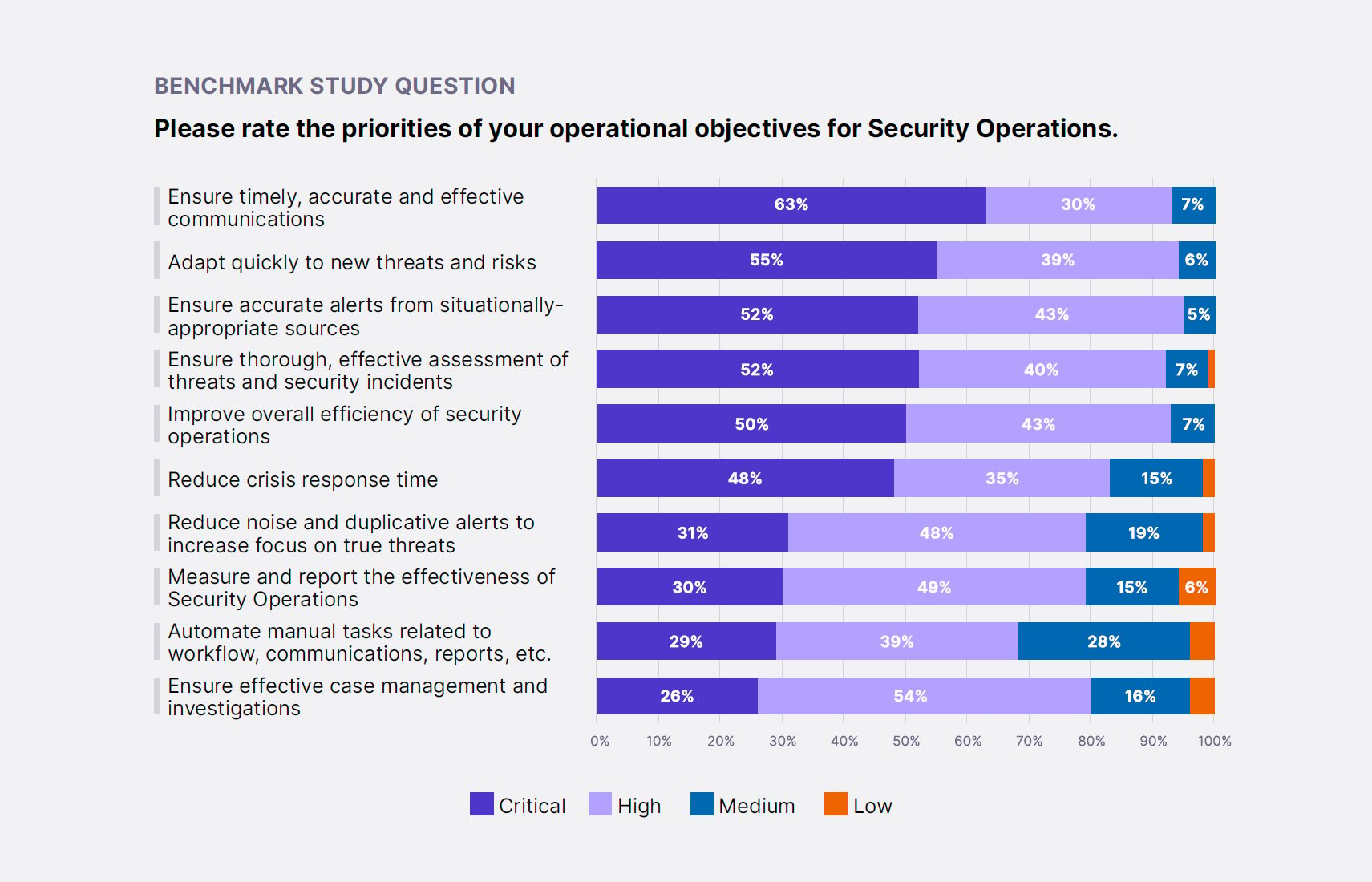
The report examined other participants’ responses who successfully met these operational objectives and identified correlations with SecOps and organizational attributes.
Respondents also ranked the importance of their strategic objectives, which are related to the overall mandate for the SecOps team and their deliverables to the organization. They are most closely aligned with the measure of effectiveness. Life safety and protection of facilities and other assets are the only strategic objectives ranked as critical by more than 50% of study participants.
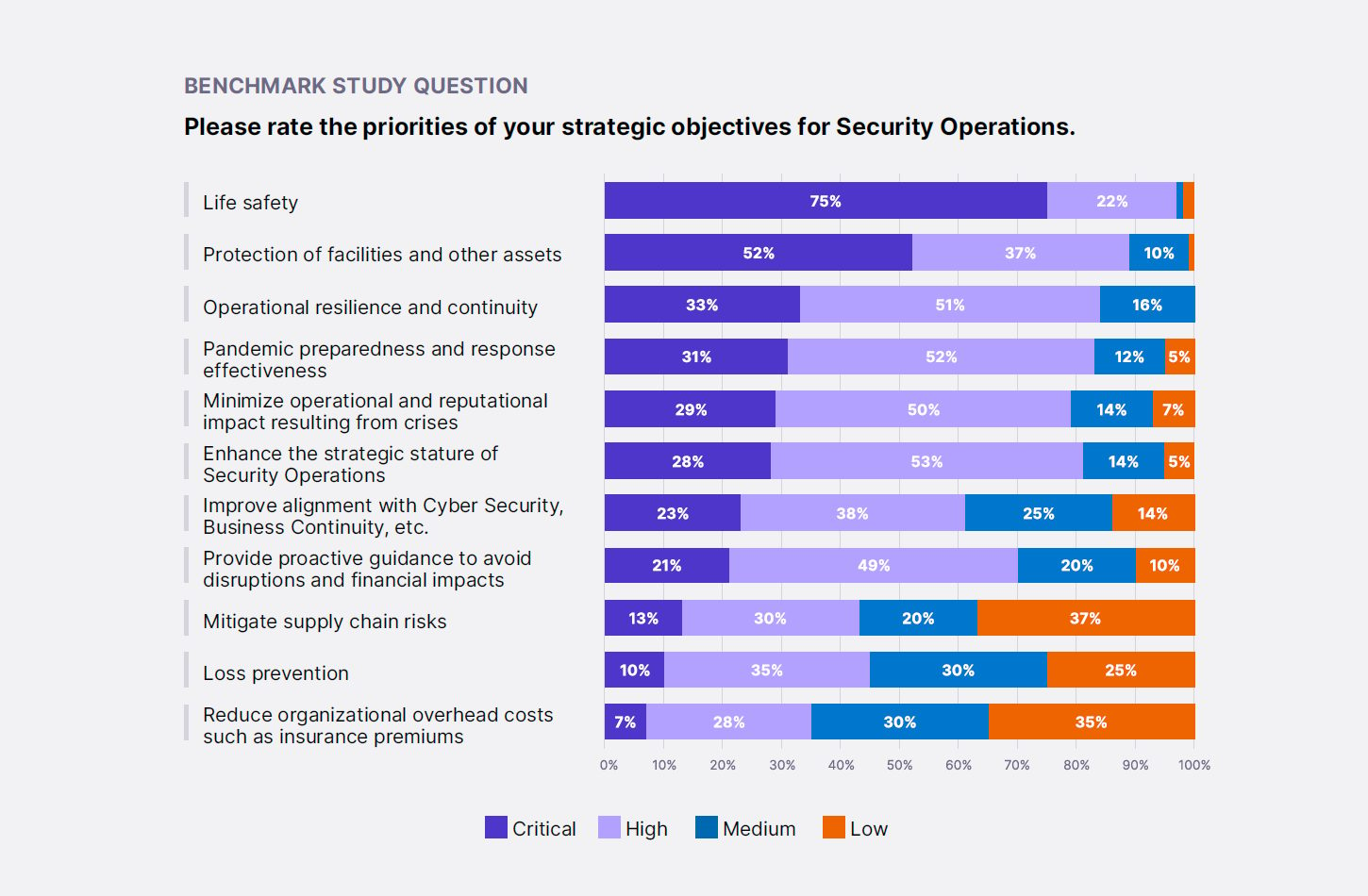
The report examined success with these strategic objectives and correlated them with SecOps and organizational attributes.
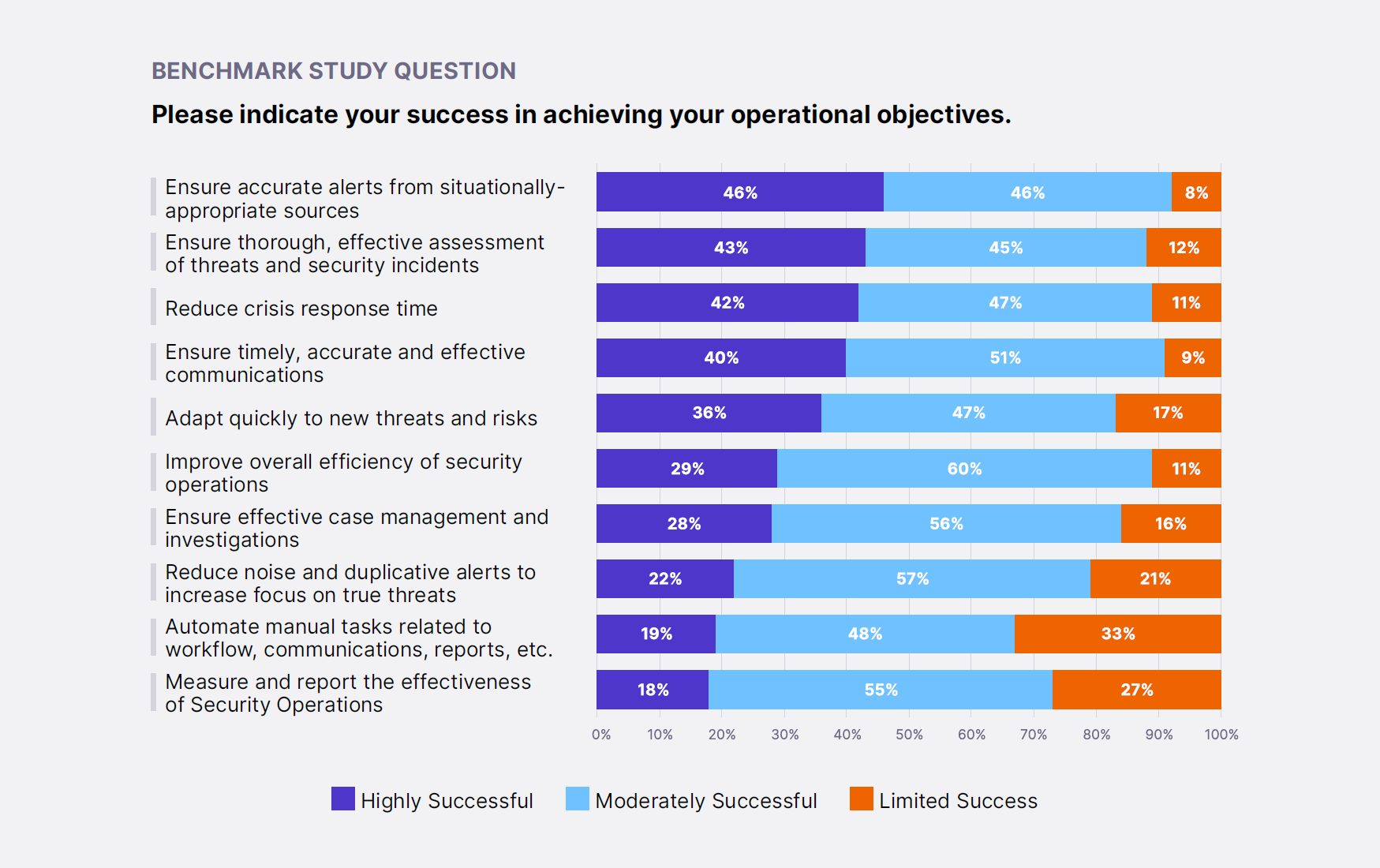
Study participants also ranked their success in achieving operational objectives. None of the operational objectives are ranked as “highly successful” by more than 50% of respondents.
The top three objectives with a high degree of success are:
- Ensure accurate alerts from situationally appropriate sources
- Ensure thorough, effective assessment of threats and security incidents
- Reduce crisis response time
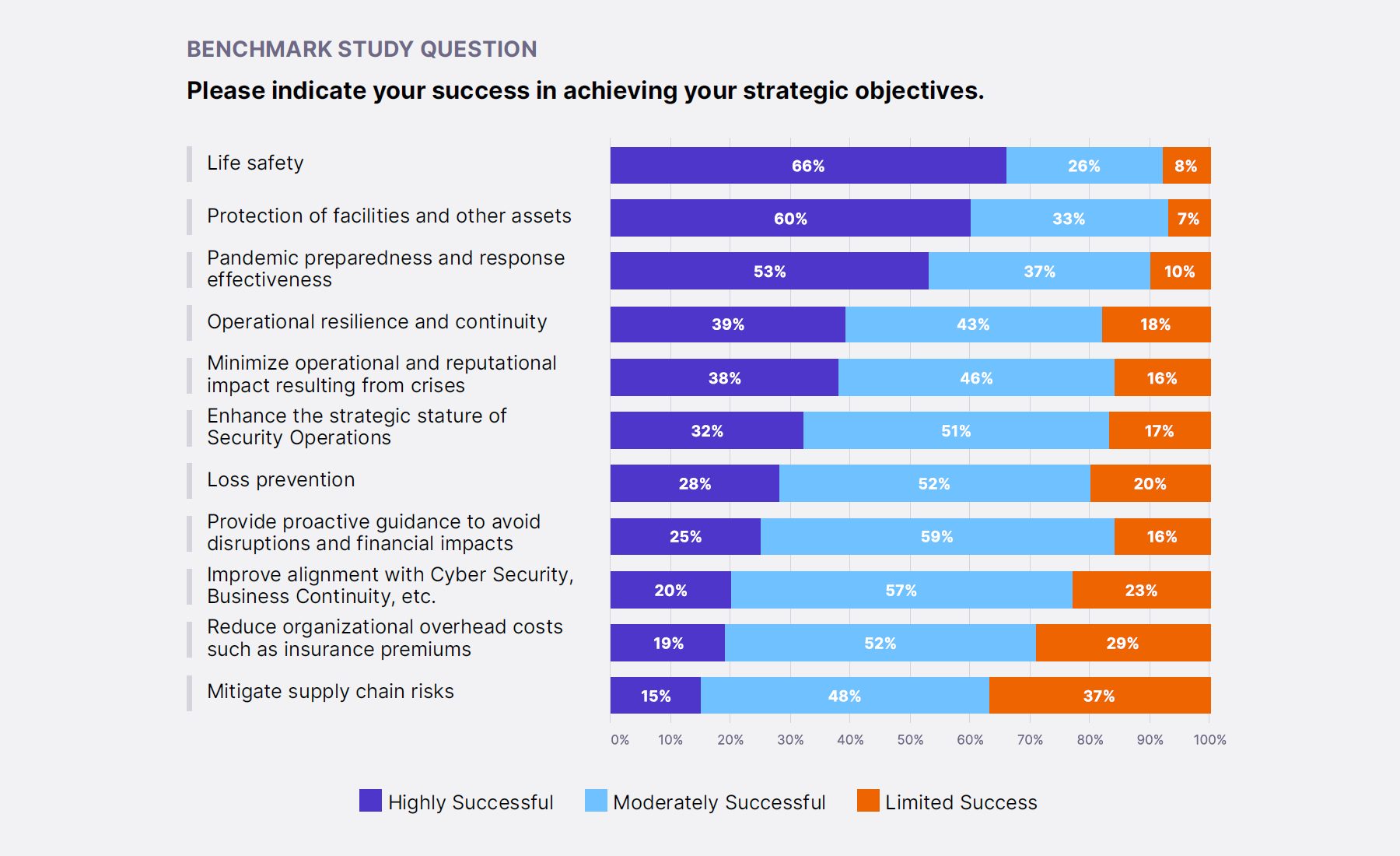
Study participants ranked their success in achieving their strategic objectives. More than 50% of study participants were highly successful with three of the four top-priority strategic objectives.
The top three objectives with a high degree of success are:
- Life safety
- Protection of facilities and other assets
- Pandemic preparedness and response effectiveness
Technology, threats, geopolitics and ideology continue to evolve and require security practitioners to update strategies, tactics, operations and policies, as well as ensure that executives prioritize security to achieve success in security operations.
For the full report, click here.
advertisement
advertisement
Amid record numbers of third-party data breaches, supply chain disruptions and the war in Ukraine, organizations are starting to adapt their third-party risk management (TPRM) programs to address new and emerging risks outside of the information technology (IT) realm, the Prevalent 2022 Third-Party Risk Management Study found. Between February and March 2022, Prevalent surveyed leaders directly involved in TPRM to understand how organizations are navigating today’s third-party challenges and staying ahead of future risks.
TPRM is at a crossroads and much more needs to be done, the study reveals. The study found seven key observations about the state of third-party risk management today:
- Organizations are paying more attention to non-IT security risks, but not enough. Information security, business continuity and data privacy and protection were rated as the top three risk types, which shows that organizations are acknowledging that third-party risk is higher than IT security risks. However, organizations continue to overlook less-quantifiable risks that could still lead to compliance violations, fines or negative reputational impacts, such as modern slavery, anti-money laundering, anti-bribery, and corruption risks.
- TPRM may be getting more strategic. Study results show that organizations are generally aligned around the strategic risk reduction goals of their TPRM programs — and that operational concerns such as cost, compliance and efficiency are secondary. Notably, executives have a fairly even view of TPRM goals across all areas, although they are primarily driven by risk reduction. Speaking of executives, more than 75% of respondents indicated that their TPRM program has more visibility among executives and the board compared to last year.
- Manual methods for assessing third parties persist, but dissatisfaction runs high. Forty-five percent of respondents indicate that they are still using spreadsheets to assess their third parties. The use of dedicated TPRM solutions grew by 14% from 2021 to 2022, and the use of governance, risk and compliance (GRC) tools and security rating services rose slightly from last year.
- Organizations are concerned with increasingly damaging third-party security incidents, but use disparate tools to detect, investigate and resolve exposures. The top concern among organizations in the survey is a third-party data breach or other security incident stemming from vendor security shortcomings. In fact, 45% report experiencing a data breach or other security incident connected to a third party in the last 12 months. Most organizations use data breach monitoring (51%), cybersecurity/dark web monitoring (45%), vendor assessments (manual/spreadsheet-based) (43%), and proactive self-reporting (43%). Organizations should be aware of the risk of using multiple, non-integrated tools to close the loop on their third-party incident response lifecycle.
- Organizations are waiting over two weeks for third-party incident resolution. 29% of respondents indicated that it would take them more than a week to determine which third parties were impacted by an incident, with 35% saying it would take up to two days to determine whether it would result in a disruption in service. 47% of respondents said it would be another week before they knew when the third party had completed its remediation or mitigation steps. It takes about two and a half weeks for organizations to remediate any third-party incident. That’s a lifetime for an organization to be vulnerable to a potential exploit.
- Third-party risk audits are getting more complex and time-consuming. Seventy-four percent of respondents said they had to report on third-party data privacy and protection controls, with information security controls coming second at 57%. Environmental, social and corporate governance (ESG) topics — a relatively new risk area — rank in the middle at 23%, and 18% of respondents indicated they had to report on human trafficking and slavery regulations.
- Third-party risk management discipline falters as vendor relationships progress. About 75% of respondents are tracking risks at the sourcing/pre-contract due diligence and onboarding stages of the third-party relationship. That leaves about a fourth of companies that don’t conduct risk assessments at this crucial stage, meaning they’re exposed to potential risks from the start of the relationship. Between 61% and 68% of respondents are tracking risks at the “business as usual” phases — assessing and monitoring ongoing management. Fewer than half of respondents are tracking contractual risks and risks at the offboarding and termination stage of the relationship.
While third-party risk management teams are making progress toward a more strategic approach to TPRM, there is still room for improvement. Security leaders seeking to grow and mature their TPRM programs as they relate to incident response, compliance and the vendor lifecycle can take three steps.
- Expand assessments beyond IT security to unify teams under a single solution and simplify audits. By unifying non-IT risk intelligence with the results of traditional cybersecurity and data privacy assessments, organizations can enrich visibility into supplier risks, elevate the strategic value of the TPRM program, and improve reporting.
- Automate incident response to reduce cost and time. Organizations should automate incident response by investing in mature tools and processes that reveal potential impacts by continuously tracking, scoring and managing cyber, business, reputational and financial risks in a single platform.
- Close the loop on the third-party lifecycle. Security, compliance and operational issues can crop up at any time during a vendor or supplier relationship, so it’s important to address risk at each stage of the third-party lifecycle.
For the full report, click here.

Third-Party Risk Management Programs at a Crossroads
XtockImages / iStock / Getty Images Plus via Getty Images
In the wake of current political instability and civil unrest, governments around the globe have advised organizations to be on high alert for potential cyberattacks, which represent a growing threat amid geopolitical conflicts. Organizations of all sizes must shift thinking toward managing elevated cyber threats and take an enhanced security stance.
A new Deloitte report, “Insights and actions: Preparing your organization for elevated cyber threats posed by geopolitical conflicts,” offers several steps to bolster security and crisis response preparedness in the days, weeks and months to come.
- Increase vigilance and proactively update indicators of compromise (IOCs) and confirm common vulnerabilities and exposures (CVEs) are fully patched; where possible, reduce digital footprints to mitigate exposure
- Confirm ingress and egress points between enterprise networks and the internet, paying particular attention to non-traditional environments such as remote access, and cloud usage
- Pay close attention to intelligence collection from government bodies and move rapidly to incorporate it into security procedures
- Identify relevant local and federal law enforcement to report a cyber incident, as law enforcement and/or government intervention may be necessary in the event of a potential state-sponsored attack
- Revise incident response (IR) playbooks, especially around data destruction and recovery and crisis communications, to ensure they are up to date. Update playbooks to include scenarios for destructive malware, Domain Name System (DNS), Border Gateway Protocol (BGP), and multiple simultaneous attacks
- Confirm (or expand) security operations coverage for 24/7, global support with proactive threat hunting
- Practice your organization’s ability to prevent, detect, contain, remediate, report, and recover from cyberattacks to confirm program capabilities and resilience
It is also critical to involve other functions that collaborate with security teams, including operations, legal and risk, human resources, and boards and executive leadership teams. Initiating these processes can contribute to stronger security functions both in response to the current elevated threat levels and as part of building high-performing programs beyond the current conflict.
Security practitioners should also consider the enterprise risks that could impact security posture — for instance, supply chain and vendor disruptions from global or multinational operations are possible and may influence normal traffic patterns or crisis operating procedures. These factors require significant strategic executive engagement to keep security and risk indicators in lockstep so that organizations can respond effectively to cyberattacks.
For more actionable steps and takeaways for executives, click here.

Bolstering Crisis Response Practices During Geopolitical Cyber Threats
Toa55/ n:iStock / Getty Images Plus via Getty Images
july 2022 / SECURITYMAGAZINE.COM


