april 2021

Product Spotlight
On Cybersecurity, Data Protection, and Privacy Solutions
By Maria Henriquez, Associate Editor
Untangle
Provides Encrypted Interoffice Connectivity Across all Sites
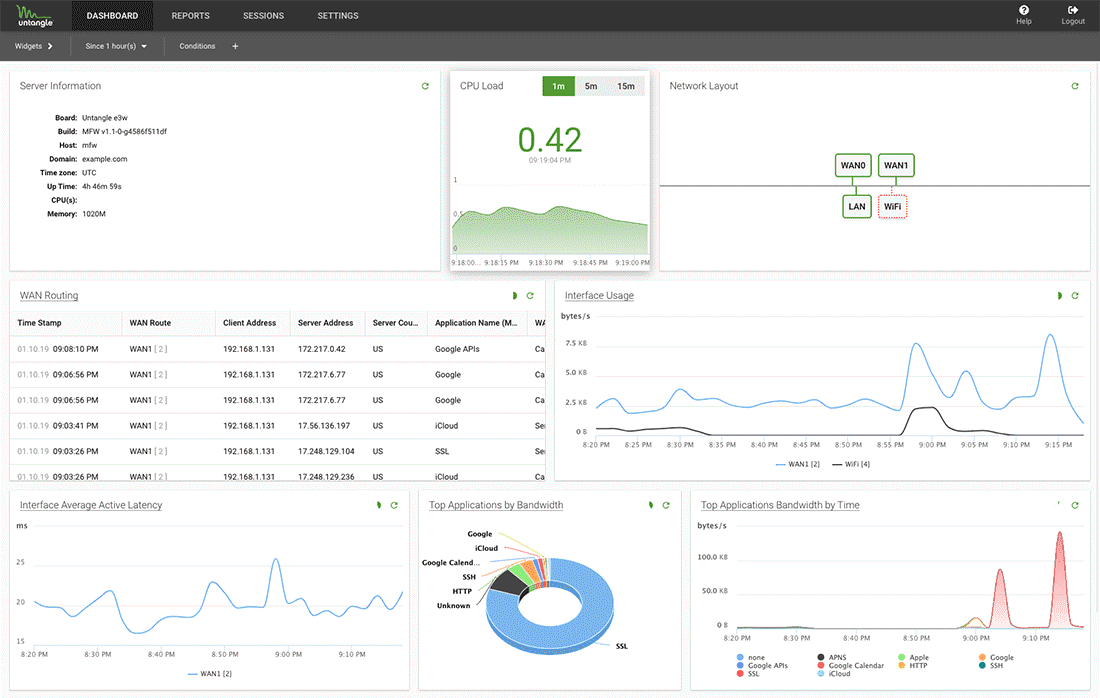
Untangle’s SD-WAN Router introduces WireGuard VPN integration to provide organizations an encrypted VPN connection to help organizations quickly set up a VPN connection between their security gateway and SD-WAN Router, resulting in a fast-performing virtual network connection. SD-WAN Router 3.0 meets the evolving needs of SMBs who have increasingly required VPN connectivity as firms manage long-term branch office and remote work plans while monitoring the ongoing COVID-19 pandemic. Centrally managed, the solution can provide encrypted interoffice connectivity across all sites, while maintaining a high level of security. Image courtesy of Untangle
Find out more at www.untangle.com
Thycotic
Manages and Defends Critical Identity Accounts and Credentials
The Thycotic Secret Server provides privileged access management (PAM) and empowers organizations to monitor, manage and defend critical identity accounts and credentials. Built to support cloud deployment, Secret Server has been designed to integrate into organizations existing cybersecurity fabric. Secret Server Cloud enables organizations to: discover, manage, and delegate access to privileged accounts with role-based access controls, military-grade encryption, multi-factor authentication support, and centralized administration; meet cybersecurity PAM best practices and regulatory obligations with immutable auditing and reporting, and event-driven email alerts; and experience rapid time-to-value, with an intuitive administration experience that empowers security professionals to configure and manage their PAM solution on their own terms. Image courtesy of Thycotic
Find out more at thycotic.com
WhiteHat Security
Continuously Scans for Vulnerabilities With Near-Zero False Positives
WhiteHat Security’s Sentinel Dynamic is a complete Application Security and Risk Management platform with integrated secure development, security testing and continuous monitoring. The SaaS platform delivers a centralized set of products and services that enables businesses to quickly deploy a scalable application security program across their entire DevOps lifecycle. Sentinel Dynamic works by combining WhiteHat’s automated Sentinel Scanner with a security expert team – artificial plus human intelligence - to provide security teams with verified vulnerabilities and actionable reports. There are three license levels of Dynamic Application Security testing (DAST) products – Baseline, Standard and Premium, each tailored to the complexity and criticality of webpages. Image courtesy of WhiteHat Security
Find out more at www.whitehatsec.com
Dynatrace
Provides Continuous Runtime Application Security for Production and Preproduction Environments
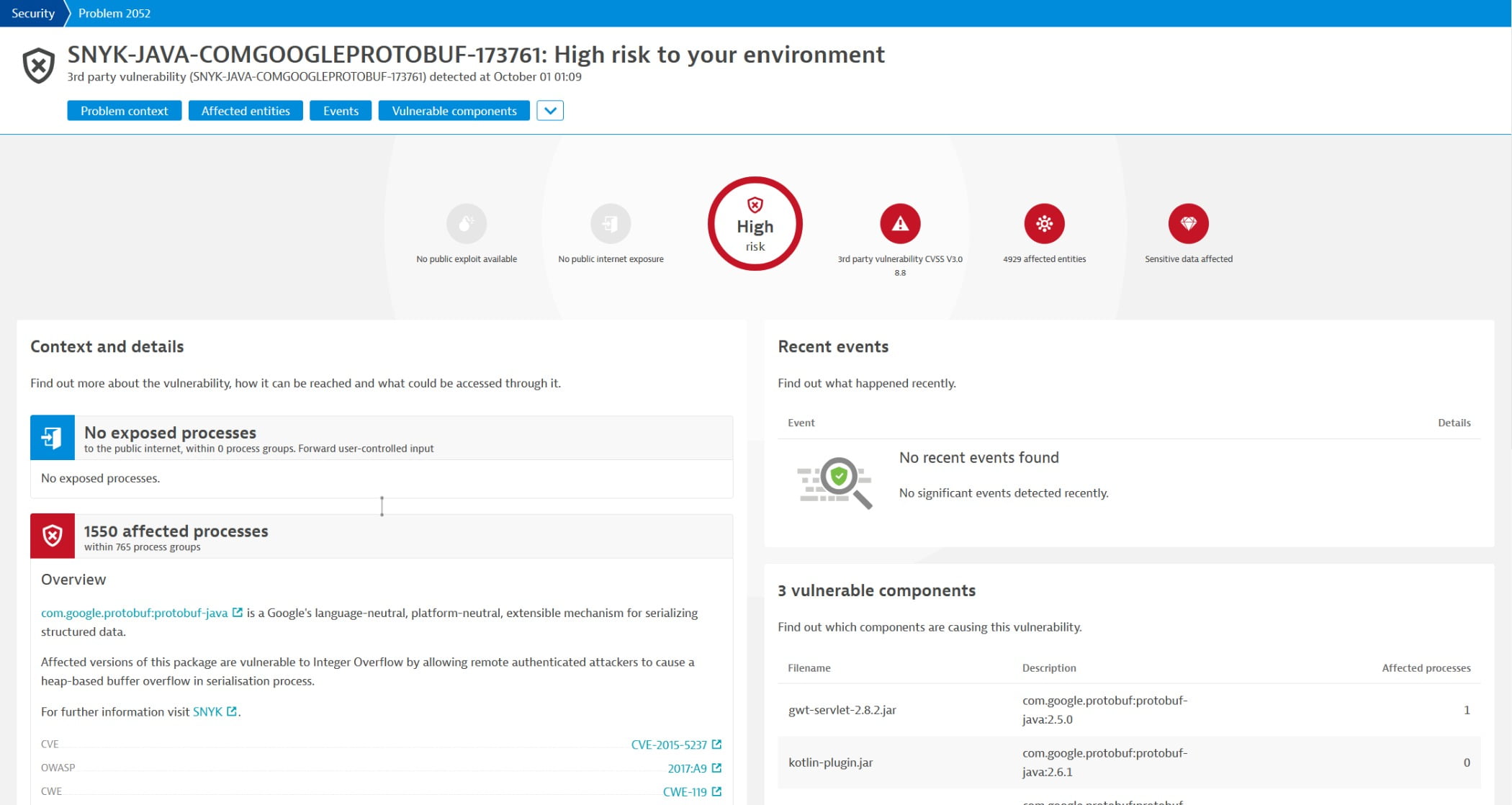
Dynatrace’s Application Security Module provides continuous runtime application self-protection (RASP) capabilities for applications in production as well as preproduction and is optimized for Kubernetes architectures and DevSecOps approaches. Dynatrace Application Security enables organizations to: identify vulnerabilities in production and preproduction environments, including what they impact and their business priority, and eliminate false positives with real-time topology mapping and distributed tracing with code-level analysis; gain vulnerability coverage and never miss a code change or new deployment with automatic and continuous discovery and instrumentation; speed up risk and impact analysis, remediation, and collaboration with Davis AI-assistance to automatically and continuously identify changes, prioritize alerts, and deliver answers about the source, nature, and severity of vulnerabilities; provides detailed vulnerability information, and ensure access to the insights needed to fix potentially compromised code through built-in integration. Image courtesy of Dynatrace
Find out more at www.dynatrace.com
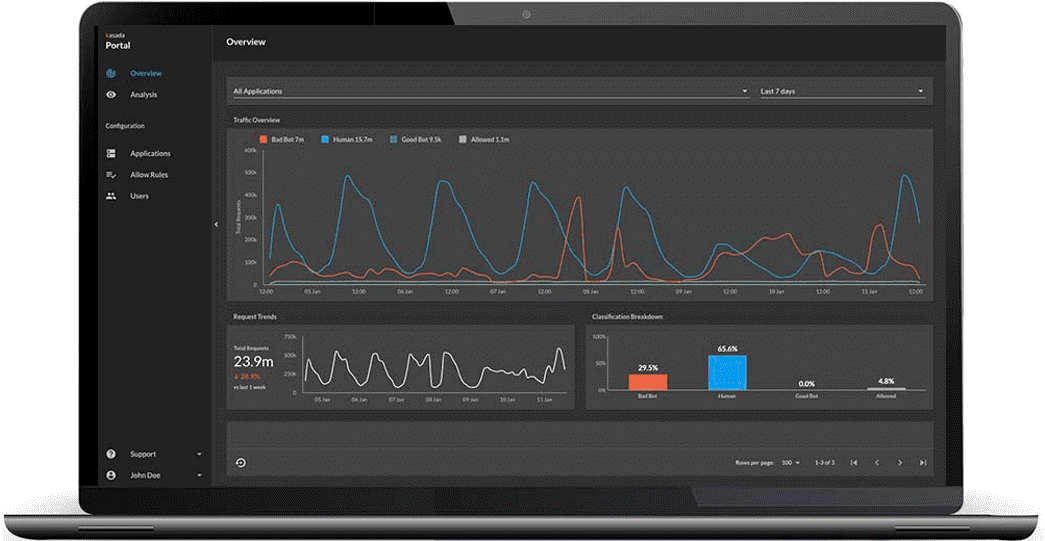
Kasada
Protects Against Bots and Evolving Cyberattack Tactics
Kasada recently announced updates to its V2 platform. To address the increasing sophistication of bot attacks, the platform provides real-time defense against advanced bots that are left undetected by traditional methods. Several improvements provide users with a long-term approach to bot mitigation without the need for burdensome maintenance. These include: 15x increase in client interrogation sensors; new proprietary and dynamic obfuscation method to make it difficult - and expensive - for attackers to retool their efforts; and additional controls for proof-of-work challenges to encourage attackers to move on to their next target. Image courtesy of Kasada
Find out more at www.kasada.io
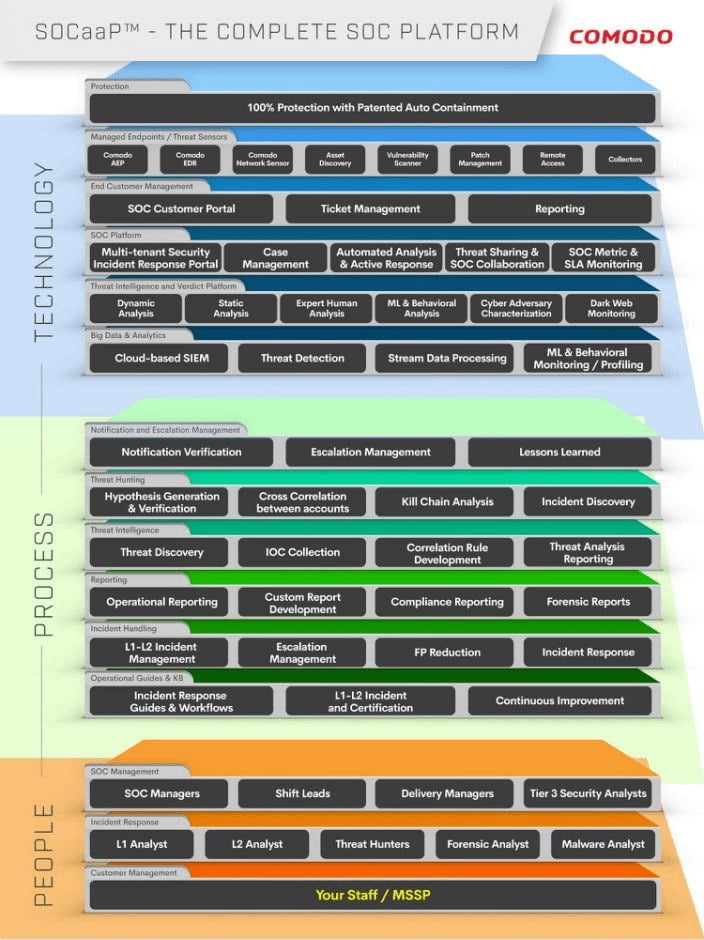
Comodo
Fully Managed or Co-Managed Threat Detection and Response Platform
Comodo’s security operations center (SOC)-as-a-Platform (SOCaaP) integrates endpoint, network, and cloud security (correlating events from both the endpoint and network) and offers white-labeled co-managed threat detection and response services. Key features of SOCaaP include: Complete integration with Comodo's Cloud-Native Cybersecurity Platform with Patented Auto-Containment technology; built-in cloud connectors that integrate with cloud services to extend visibility over cloud assets and workloads; a single pane of glass combining all security service operations, customer onboarding status, actionable alerts, and escalations into a single dashboard; and a cloud-based, multi-tenant next-generation security information and event monitoring platform (SIEM) for MSPs including an event correlation engine. Image courtesy of Comodo
Find out more at www.comodo.com
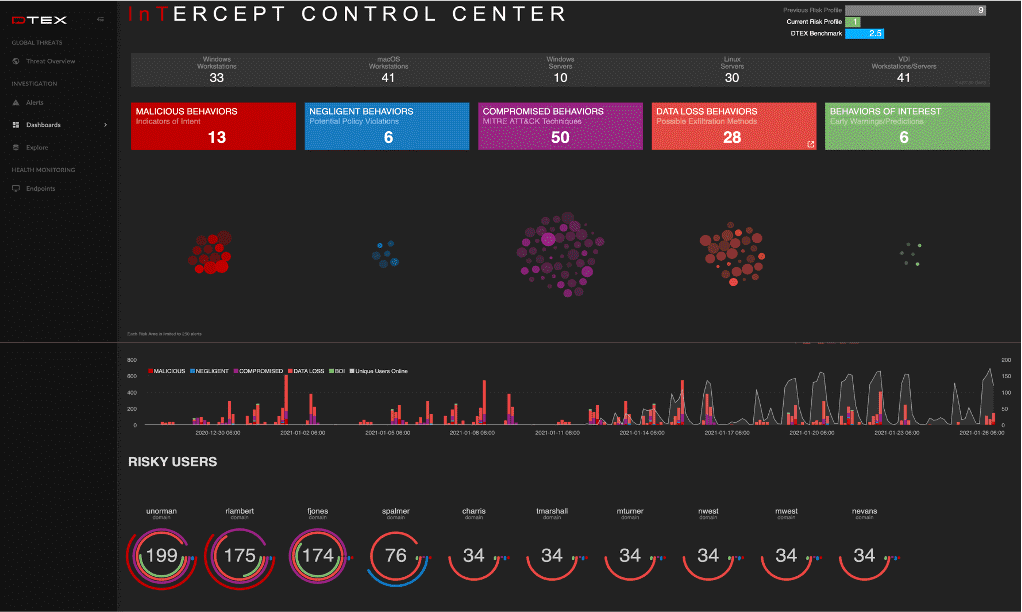
DTEX
Mitigates the Risk of Data and IP Loss
The DTEX InTERCEPT 6.5 platform brings together the capabilities of user and entity behavior analytics (UEBA), endpoint data loss prevention (DLP), digital forensics and insider threat management into a cloud-native platform to empower customers to mitigate the risk of data and IP loss. Specific capabilities and features that have been introduced and enhanced as part of this latest release include: sensitive IP and customer data alerts; interactive data lineage map; and data classification policy templates. The platform supports regulatory compliance with emerging data protection regulations, including HIPAA, CCPA, GDPR, SOX, PCI DSS, ITAR and more. Image courtesy of DTEX
Find out more at www.dtexsystems.com
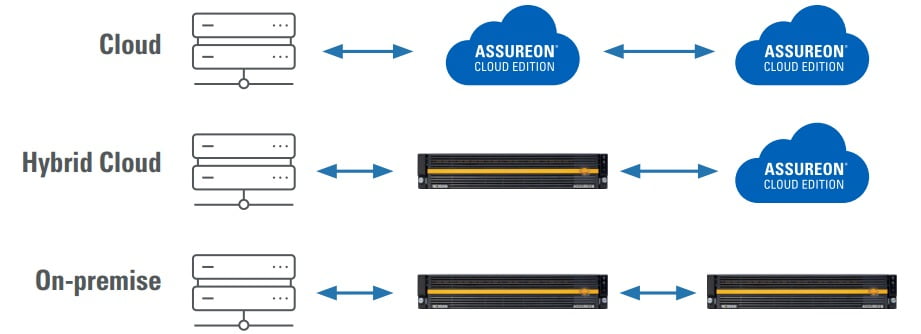
Nexsan
Ideal for Protecting Data and Backups om Cyberattacks and Ransomware
The Nexsan Assureon Cloud Edition acts as an immutable active data vault and delivers flexible deployment options as a cloud, hybrid or on-premise solution. It is ideal for protecting unstructured data and backups against cyberattacks and ransomware, ensuring regulatory and corporate compliance, providing secure storage for reusable content, and for storage optimization. The solution can protect backups from malware, ransomware attacks, or user error so organizations can recover files from a worst-case scenario situation. It protects data with file fingerprinting and asset serialization processes, in conjunction with metadata authentication, private blockchain and a data verification algorithm. Image courtesy of Nexsan
Find out more at www.nexsan.com
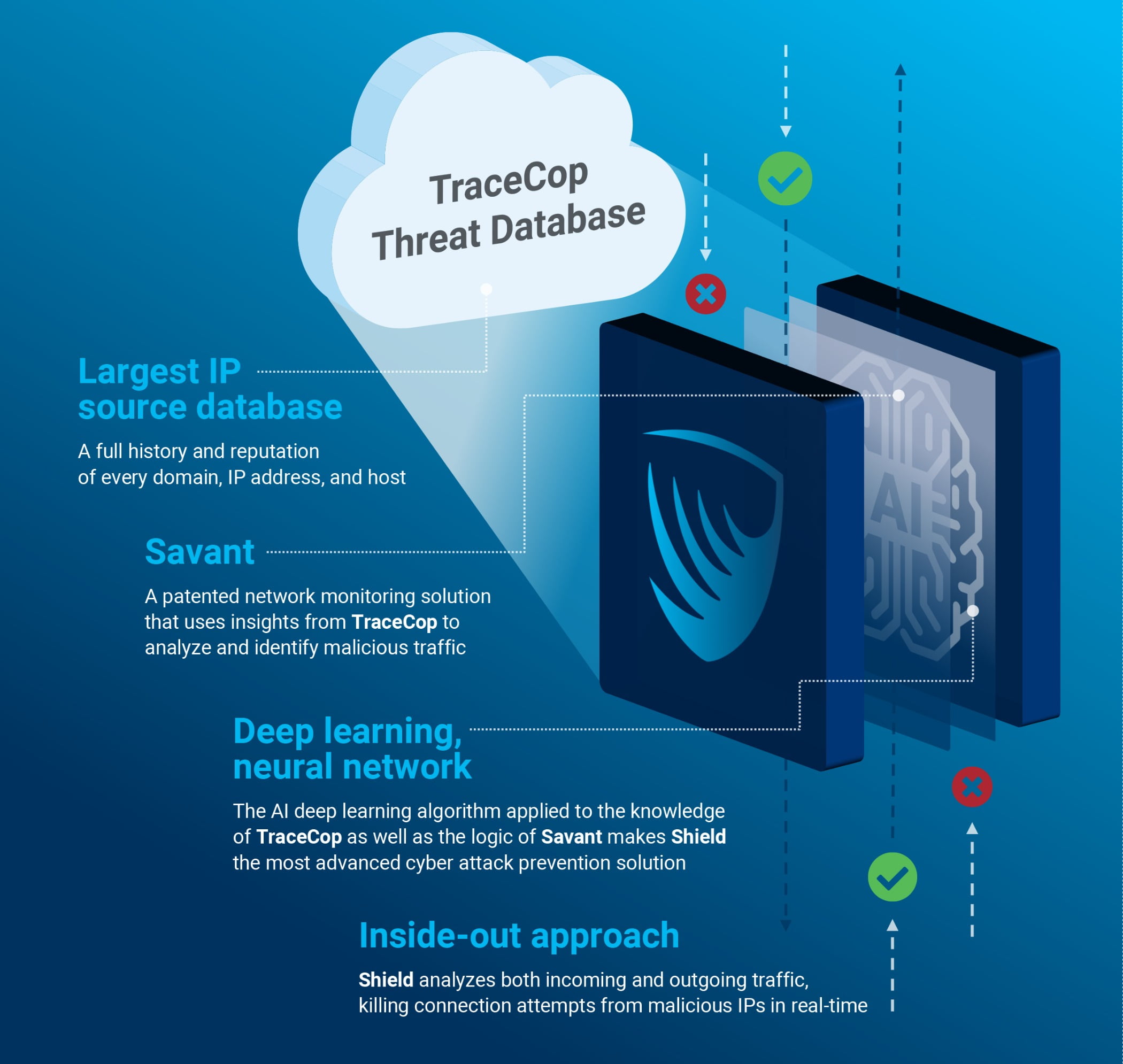
INTRUSION
Brings Government-Level Cybersecurity to Business
INTRUSION Inc.’s Shield aims to take a new approach to protecting an organization’s network by not only alerting to cyber threats but immediately neutralizing them. Shield combines plug-n-play hardware, software, global data and services, along with real-time artificial intelligence (AI), to deliver a layer of cyber defense for businesses. Shield works on the premise that cybercriminals already exist within the user’s network, which means Shield is constantly monitoring all incoming and outgoing traffic. Using its Process-flow Technology, the solution applies signatures and rules based on DNS, TCP, UDP – and the connections between DNS and IPV4 and IPV6 addresses – to learn the behavior and patterns of cybercrime activity. Shield then continuously monitors incoming and outgoing traffic to identify new threats. Image courtesy of INTRUSION
Find out more at www.intrusion.com
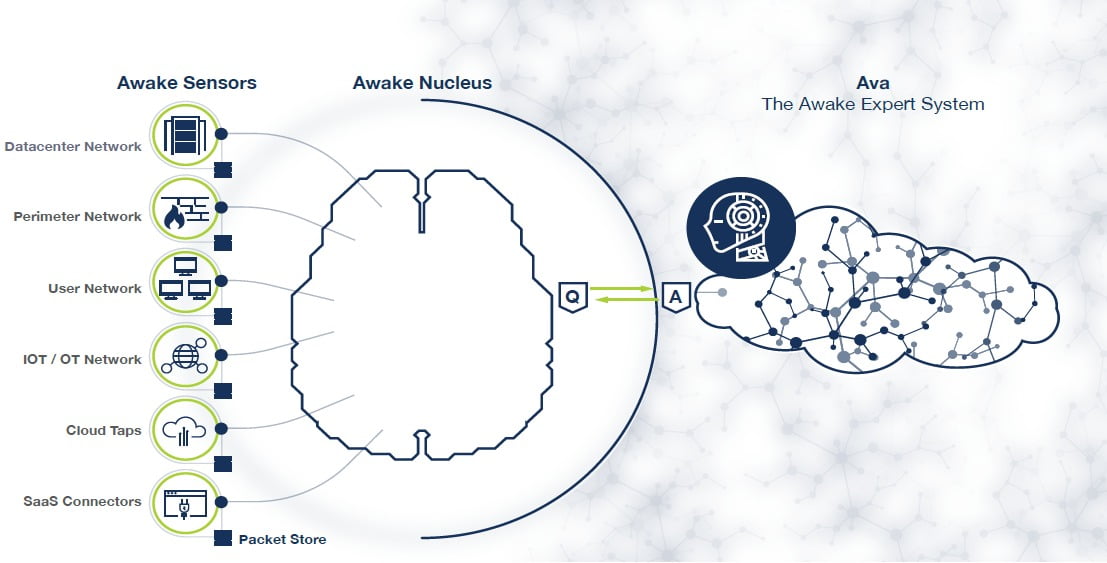
Awake Security, a division of Arista Networks
Offers Network Detection and Response Across Cloud, Hybrid and IoT Environments
Awake Security, the network detection and response (NDR) security division of Arista Networks, unveiled platform enhancements that strengthen its ability to detect advanced threats, protect the unmanaged attack surface and autonomously perform threat hunting and forensic investigations. Key capabilities now available with the Awake platform include: autonomous unmanaged device discovery and risk tracking; autonomous threat hunting and investigations; and intelligent role-centric user experience. Image courtesy of Awake Security, a division of Arista Networks
Find out more at www.arista.com
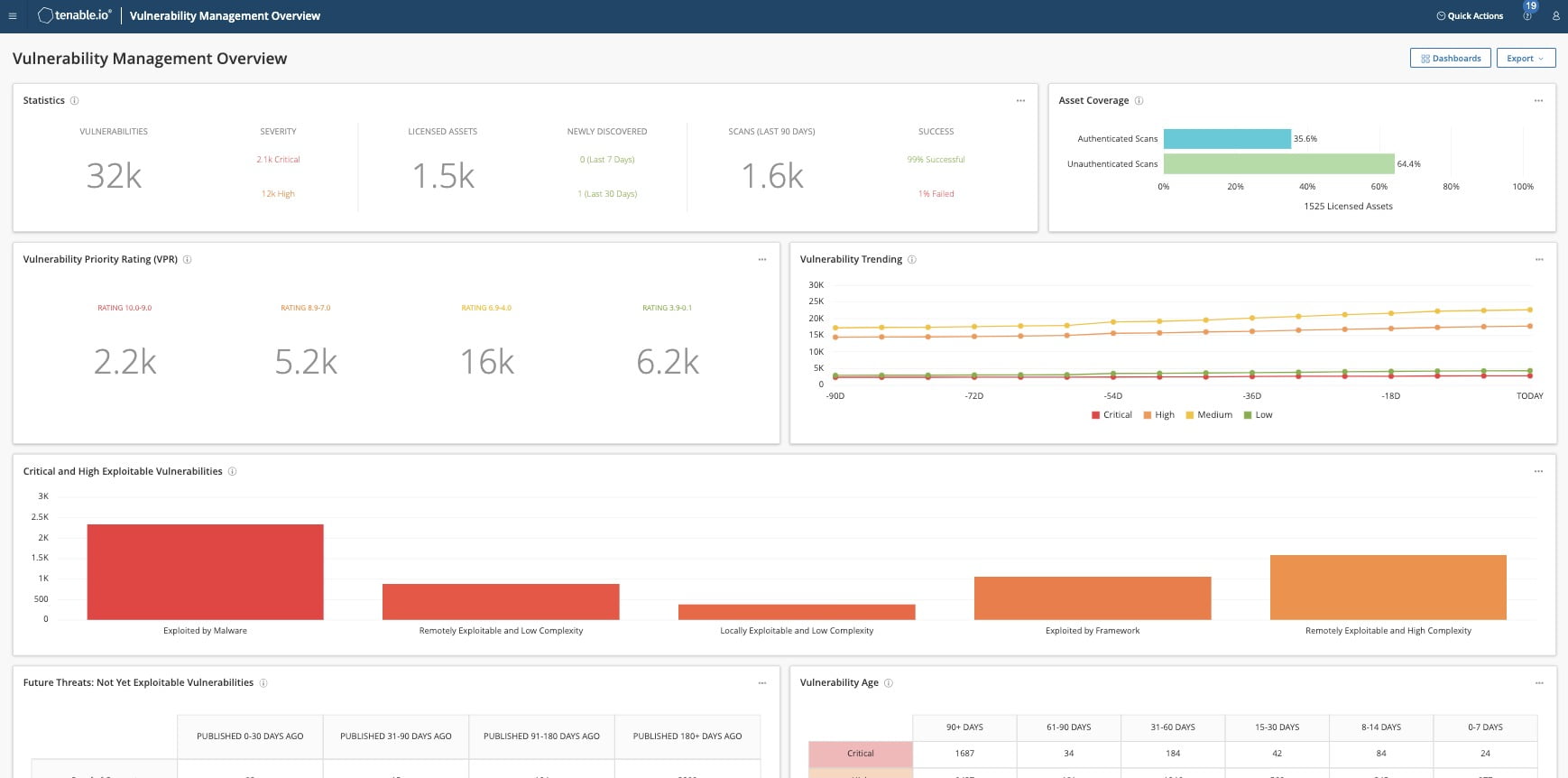
Tenable
All-in-one Risk-based Vulnerability Management Platform
Tenable, Inc.’s Tenable.ep is an all-in-one, risk-based vulnerability management platform designed to scale as dynamic compute requirements change. Tenable.ep combines the company’s Vulnerability Management, Tenable.io Web Application Scanning, Tenable.io Container Security and Tenable Lumin – into one platform, enabling customers to see all of their assets and vulnerabilities in a single dashboard alongside key threat, exploit and prioritization metrics. Moreover, Tenable.ep’s single, asset-based licensing model frees organizations to dynamically allocate licenses across all asset types according to their unique attack surface and modify as their environment changes. Image courtesy of Tenable
Find out more at www.tenable.com
Volante
Combines a Cybersecurity Solution With Ransomware-only Insurance
Volante Global’s Cyber LockoutSM combines ransomware insurance cover with the latest in cybersecurity technology. A multi-layered cybersecurity solution, Cyber Lockout integrates Trident Lockdown, provided by GBMS Tech, which is built to prevent malware, including those introduced through zero-day vulnerabilities, from executing in the user’s computer systems. In addition, it offers a ransomware-only insurance policy providing cover for the costs of recovering from a ransomware attack, including breach counsel costs, fees relating to computer forensic services, data restoration costs, ransomware payments, and business interruption-related losses, if applicable. Image courtesy of Volante
Find out more at www.cyberlockout.com
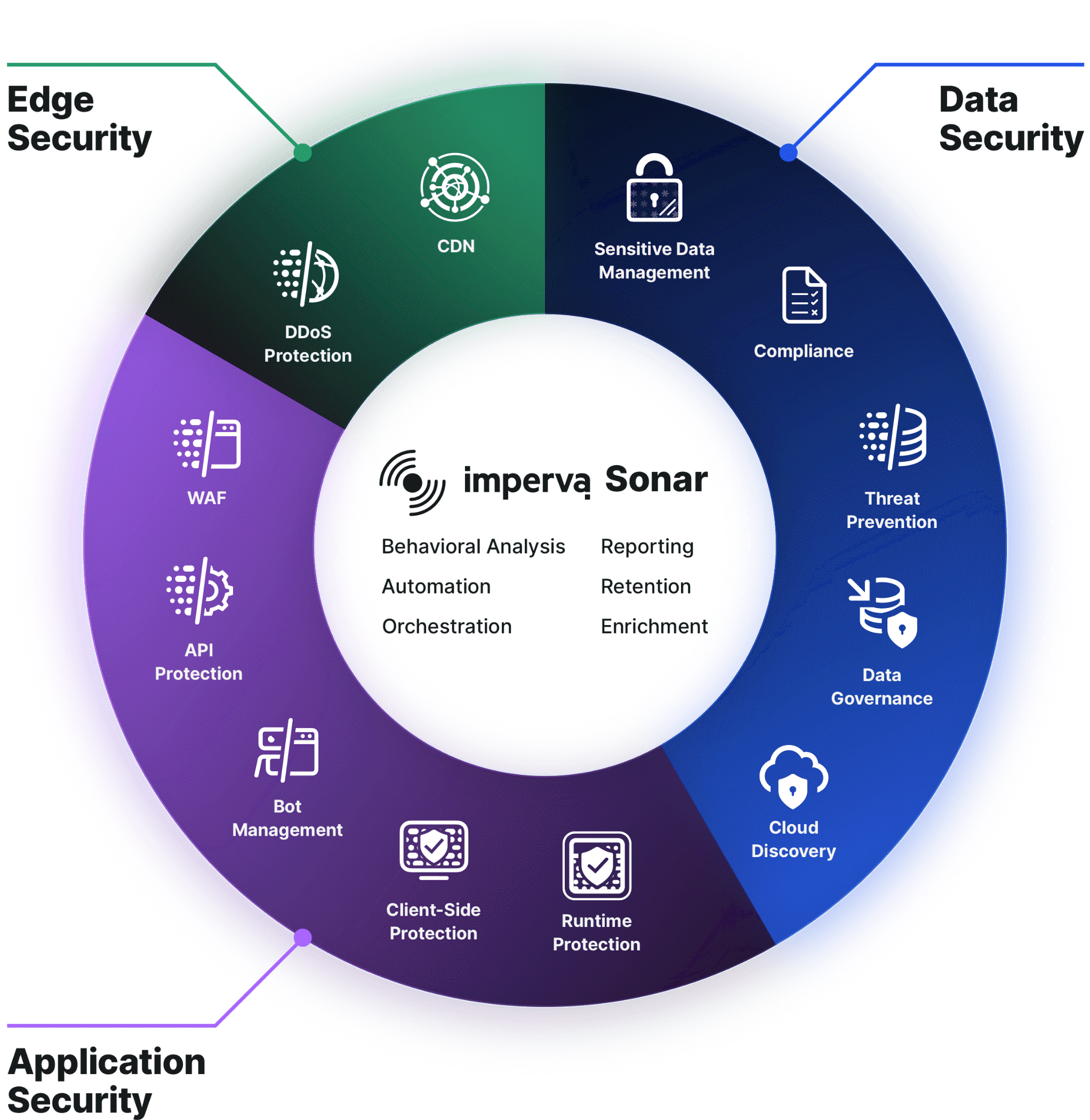
Imperva
Eliminates Need for Siloed Point Solutions
Imperva, Inc.’s Imperva Sonar platform helps eliminates the need for siloed point solutions and delivers integrated analytics while automating workflow and accelerating incident response. Advanced analytics provide visibility to two challenging information security blind spots: the applications where breaches most often originate and the data most targeted for theft. Its new integrated unified management console ties together all aspects of the Imperva Sonar platform into one dashboard, including security performance metrics, attack analytics, and suspicious traffic for investigation. Users have visibility into mitigated DDoS attacks occurring simultaneously with bots abusing APIs. The simplified user interface surfaces key risk areas via machine learning and enables one-click resolution capabilities, helping resource-constrained security teams resolve issues faster. Image courtesy of Imperva.
Find out more at www.imperva.com
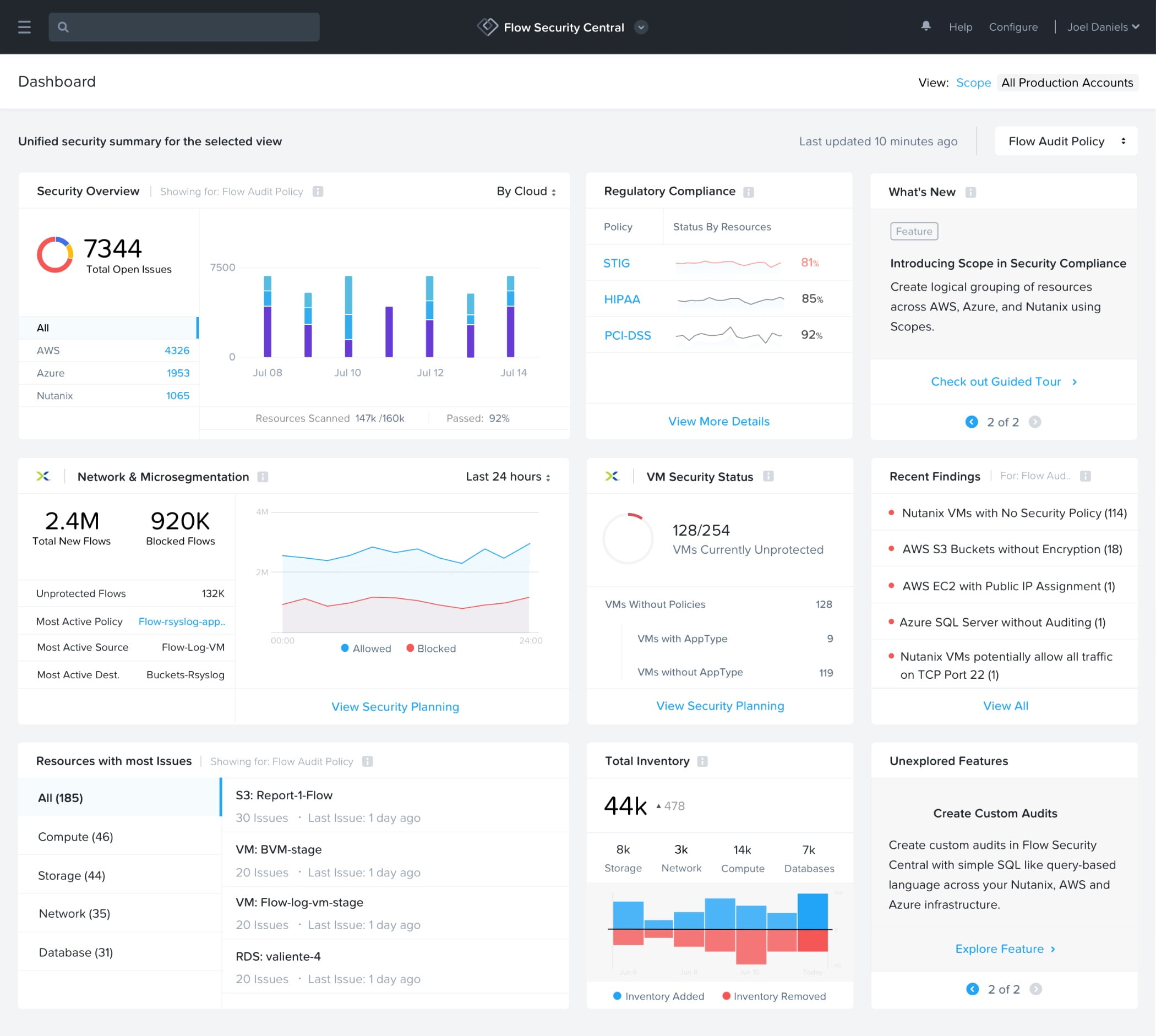
Nutanix
Includes Ransomware Detection for File Storage Services
Nutanix announced additional ransomware protections in the company’s cloud platform. These include new threat monitoring and detection, as well as more granular data replication and robust access controls, all natively built into the Nutanix stack. These new capabilities build on network security, files and objects storage, virtualization, and business continuity to help enterprises prevent, detect and recover against ransomware attacks across multiple cloud environments. The Nutanix cloud platform now includes features within the object storage solution, Nutanix Objects. Objects includes more granular permissions to access object data for primary and secondary storage. Specifically, Nutanix Objects now offers the ability to configure Write Once Read Many (WORM) policies for individual files and objects selected by an IT team to help guard against unauthorized deletion or encryption of data, thwarting many common ransomware attacks. Image courtesy of Nutanix
Find out more at www.nutanix.com
april 2021 | securitymagazine.com
READ MORE


